Cyber security | 10 February 2021
Cyber security management in the chemical processing industry
Published by Graham Foss
Cyber security Management refers to the collection of processes, practices and procedures required to protect a company’s cyber assets. This includes preventing computer networks and integrated devices from data corruption, unauthorised access, and cyber attack.
What is Cyber Security Management?
Cyber security Management refers to the collection of processes, practices and procedures required to protect a company’s cyber assets. This includes preventing computer networks and integrated devices from data corruption, unauthorised access, and cyber attack.
All industrial sectors that use computer technology for automation, control, and information storage must consider cyber security management. Local and international regulations exist to advise, monitor and in some cases, police, the adherence of companies to the standards required to operate within their region.
Different disciplines, such as Information Technology, Cryptography and Criminology feed into the planning and application of Cyber Security. The simple goal is the securing of networks and facilities from the threat of cyber attack.
What is a Cyber Attack?
A cyber attack is an unauthorised attempt to access a computer network using malware, viruses, or social engineering. This is to inhibit, inconvenience users, embarrass companies, or steal information.
Social engineering techniques such as phishing, catfishing or any other form of trickery are the most common. For most people, even in their private lives, receiving a suspicious e-mail is a daily event.
These types of threat can launch from anywhere in the world. However for cyber attacks, this may also include local concerns such as site access, unsecured connections, unintended employee actions, physical theft or sabotage.
Dangers in the Chemical Industry
As technological interconnectivity increases and terms such as the ‘Internet of Things’ and the ‘Fourth Industrial Revolution’ become more realised, the benefits from such intricate networks increase, but so do the risks.
The chemical industry, as it becomes more computer controlled and automated is far from immune from cyber attack. In many ways, it is a prime target for those that want to steal, damage or cause mayhem. Cyber attacks may not simply expose information or affect production but may also corrupt or influence computer systems. This is to push equipment out of safety limits, causing physical damage to equipment, or even people. The inherent danger in many chemicals themselves also increase the risk to life.
Leaking of Sensitive Data and Client Information
At a less dangerous level, cyber attacks may cause the leaking of sensitive data, client information, or the violation of safety and environmental standards. Although less harmful, such attacks could still mean the closure of a facility, through lack of customer trust or regulation breach. This is just as easily as an explosion or leak could.
Studies have shown that some of the danger arise from many facilities having a mixture old and new equipment. Getting an overview of all the equipment in a facility and how it connects to everything else can be a vast challenge if it has never been done comprehensively before.
With control software being potentially held in various electronic or paper methods, or indeed not at all, responding to a cyber attack in an appropriate and timely manner becomes all but impossible.
What are the dangers to the Chemical Processing Industry?
The scale of the problem is vast, and the chemical industry possesses some unique dangers. For example, over 3000 facilities in the US are ‘high-risk’. This mean means they use at least one ‘chemical of interest’. This includes toxic, explosive or other potentially weaponizable compounds.
One of the most well-known cyber attacks on the chemical industry occurred in 2017, during the attack of a petrochemical facility in Saudi Arabia. The attackers accessed a critical safety system with malware known as ‘Triton’. It exploited a bug in the Windows operating system. The potential for disaster was so big it became known as “the world’s most murderous malware.”
Other systems besides the most critical or dramatic are targets for cyber attack. Non-safety systems such as HVAC or Business networks may also be targets. While there may be less immediate consequences, this can result in loss to reputation and revenue.
Combating Cyber Attack
The existing physical protection of a chemical facility, the chain-link fences, the lockable doors, and security cameras are part of the protection against cyber attack. This is because the relationship between physical security and cyber security is very interlinked. One protects the other, and without a lock on the server room door, the best cyber security in the world becomes worthless.
It is not enough to protect only one part of the facility, as a defense strategy is only as strong as its weakest link. It is vital to understand potential risks, and how to prevent or control them. Create policies and processes suited to the requirements of particular areas is also important.
There needs to be a system of multiple detection and preventative measures. This includes layers of protection, complementing each other providing defense in depth, and clear plans and contingencies. This increases resilience from cyber attack is the aim of a good cyber security plan, whatever the industry.
This is time-consuming and costly, but there are some quick wins available. This includes taking, storing, and regularly testing backups as part of a Disaster Recovery plan.
In any facility that uses networks and computer-controlled machinery, cyber security should become a standard concern in any risk management strategy meeting.
Governments, Organisations and Standards
ISA 62443 lays out cyber security plans, processes, and procedures for securing and defending industrial plants from cyber attack. ISA 62443 is not specifically tailored to the chemical industry but does offer an approach. This includes creating a comprehensive cyber security management system (CSMS).
Chemical companies in the US follow the CFATS (Chemical Facility Anti-Terrorism Standards) guidance for cyber security. This standard has evolved over time, via legislation and executive order. It includes not just physical attacks from terrorists, but cyberattacks by anyone.
Slow to adapt at first, US Industry experts have realised that the CFATS must define a process that can be put in place to meet new and unexpected threats. The CFATS is also adapting to consider the continuous changes in technology that provide gaps that cyber criminals can exploit.
Some recent reports, such as from the GAO (Government Accountability Office) in 2015 have been fairly scathing of the lack of preparedness in US chemical plants. This complacency becomes more dangerous as the world becomes more interconnected and the incident level of cyber attack increases.
In addition, US Chemical companies that are members of the ACC (American Chemistry Council) are required to identify cybersecurity threats, implement plans to counter them and to train employees where required.
European Regulations in relation to Cyber Security Management
In Europe, the European Union General Data Protection Regulation (GDPR), while primarily aimed at protecting EU citizens, also contains regulations on protecting industry from cyberattack.
The GDPR puts the onus on companies to protect themselves and notify authorities in the event of cyber attack. This increases transparency and to prevent companies from hiding breaches, in an attempt to limit reputational damage.
In the United Kingdom, the HSE (Health and Safety Executive) released new guidance on the Operational Guidelines for IACS.
The HSE recognise that there are significant actions required to get UK plants compliant with the guidelines. In addition, such government initiatives as the Cyber Security Information Sharing Partnership (CISP), encourage UK industry to work together.
How things changed in 2020
The chemical industry is as an essential part of national infrastructure throughout many countries. It is of equal importance to the energy, water, and food sectors. The link between the chemical and pharmaceuticals sector makes the protection of plants even more important.
Almost everyone that works, now works in a different way from how they worked in 2019. Many employees that were previously office-based now work at home, creating the need for increased security around logging in, password protection and authentication. Many industrial workers must still work at their plants, but the additional infrastructure required to keep people safe from COVID-19 infection is an extra burden that requires assessment, control, and management.
How Asset Guardian can help
Cyber threats to the Chemical Industry are on the increase leading to the requirement for increasingly sophisticated defenses.
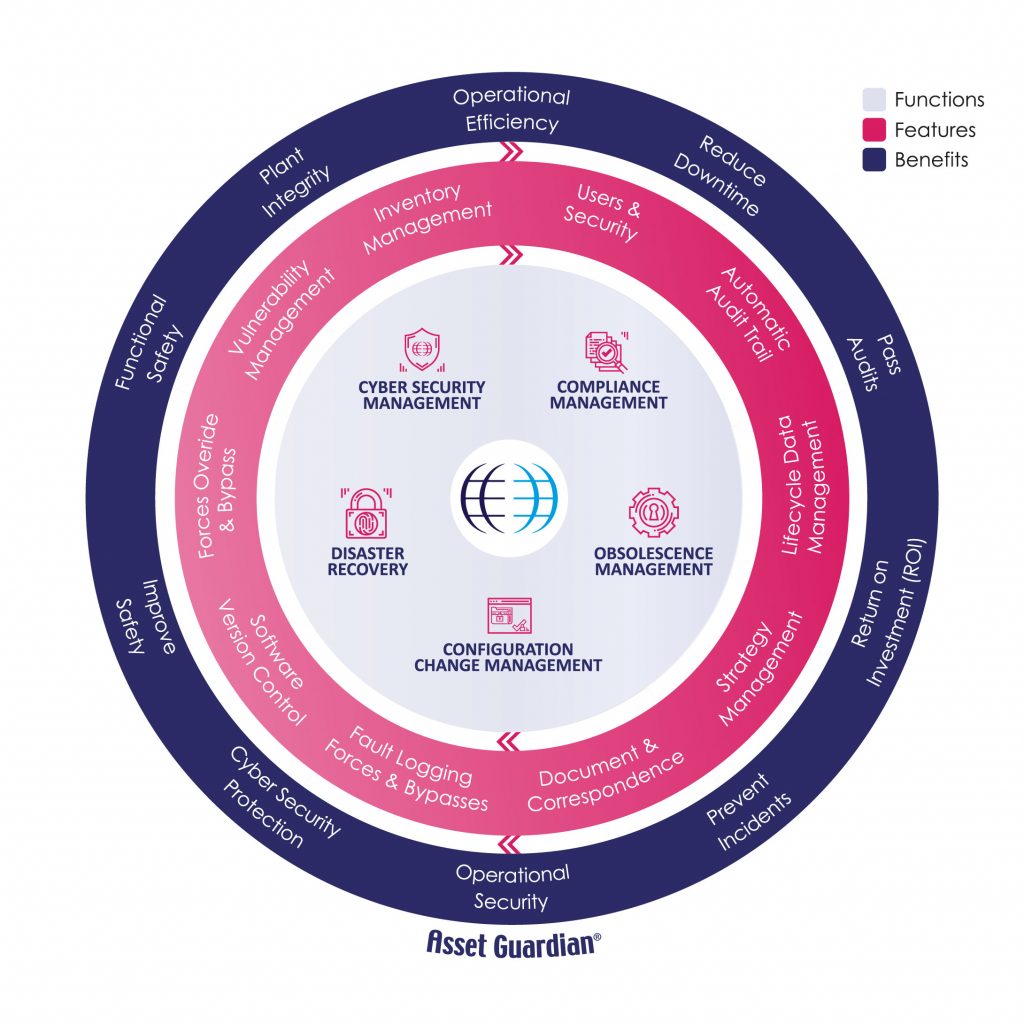
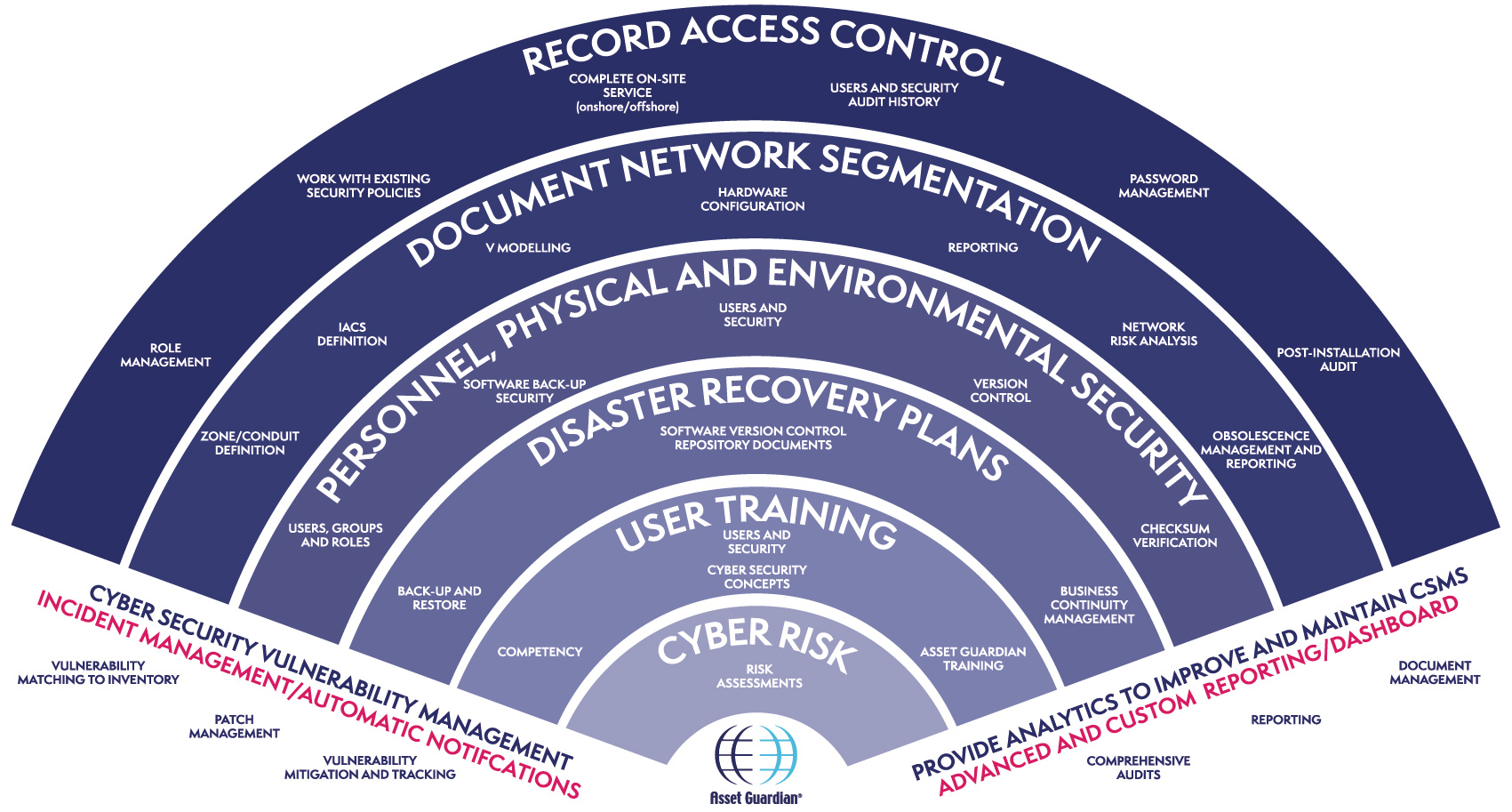
Standards such as ISA 62443 require that a facility at risk from a cyber attack protects itself through the use of a CSMS (Cyber Security Management System).
Cyber attacks come in many forms, and while recent ransomware attacks have been more newsworthy and spectacular, more common, and insidious forms of attack such as phishing and pretexting are just as dangerous. Rigorous authorisation and authentication systems and through user awareness training can counter these.
Another key defense against cyber attack is the use of a Disaster Resilience and Recovery plan. A key part of the recovery plan is to ensure the regular storing of backups in a secure location isolated from the live system.
The use of an integrated solution can benefit organisations that face cyber security threats as these threats rarely occur in isolation. A solution that also records and tracks all other aspects of the industrial complex is beneficial. This includes configuration and obsolescence management. This will ensure compliance to industry standards, and aid in disaster recovery, user management and auditing.
Looking for a an OT Cybersecurity solution? Get in touch today.