Cyber security | 31 January 2018
Cyber security management system for leading oil and gas operator
Published by Graham Foss
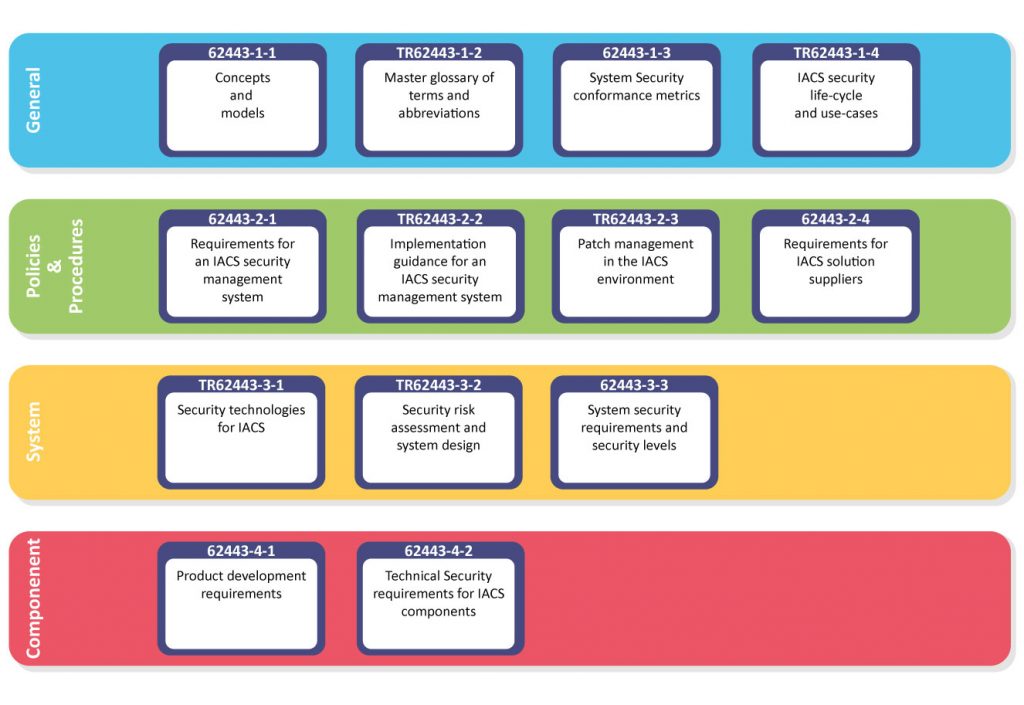
A major oil and gas operator undertook to protect itself from the ever increasing threat of cyber attack. In order to do this, they sought to comply with the industry standard IEC 62443 which is the cyber security standard specific to the Controls and Automation industry.
Challenge
It comprises standards, reports and procedures pertaining to industrial control systems cyber security in a controls and automation environment defined and known as an IACS (Industrial Automation and Control Systems). In the case of this particular oil and gas operator, the area that was required to meet the standard consisted of nine offshore sites and two onshore.
The main challenges faced by the Oil and Gas operator were:
- As their systems became more and more integrated, they became increasingly vulnerable to Cyber Security threats for instance phishing, water-holing, ransomware and malware.
- These threats could be launched from anywhere in the world and originate from apparently trusted sources
- Offshore facilities that used to be considered safe by existing in virtual isolation were becoming more vulnerable due to forms of potentially unsecured connections such as USB, Wi-Fi, and Blue Tooth.

Solution
The IEC 62443 standard is written to combat these threats and it specifies the use of a CSMS (Cyber Security Management System), a robust cyber security framework. A CSMS defines the business’s entire cyber security strategy, which includes the use of a computer based system to track everything related to protecting against all forms of cyber attack.
The oil and gas operators were already aware that they had Asset Guardian installed on all of their onshore and offshore sites. It was being used to provide a single repository for storing the data of programmable systems, supporting access to data both on and offshore, providing effective PLC code management and as part of their disaster recovery strategy.
After review, it was decided that rather than paying for another software package dedicated to cyber security, Asset Guardian would be used as the system required as part of the CSMS as defined in IEC 62443.
Result
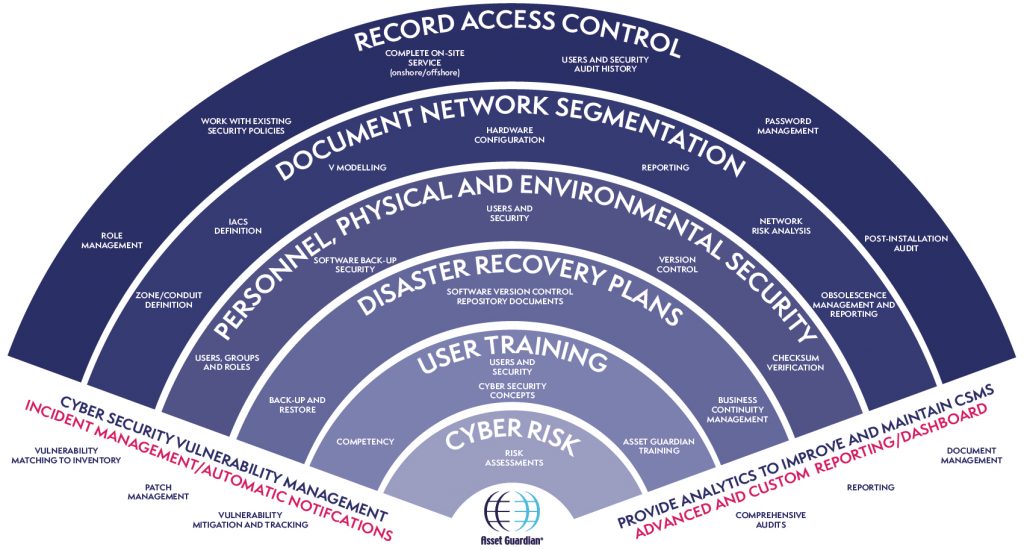
It was found that with Asset Guardian, not only was the network architecture in place, but there also existed a wealth of data and information entered into the database that already filled many of their requirements. Asset Guardian’s systematic approach to handling access, logging and managing of information, and software was well suited for use as a CSMS and would add value to their initial investment. In fact, Asset Guardian already offered the functionality to manage cyber security issues such as:
- Patch levels and software upgrades
- Identify cyber security risks
- Organise user training
- Improve existing business continuity and disaster recovery plans
- Organize and structure personnel, physical and environmental security
- Document network segmentation
- Record Access Control (i.e. Administration/Authentication/Authorization)
- Cyber Security Incident Reports
- Provide Analytics to improve, develop and maintain the overall CSMS
Asset Guardian was also already an important component of the Operator’s Disaster Recovery Plan. Software held in Asset Guardian was split over nine offshore sites, with a Leader server held at the head office. In the event of data loss in any of the sites they could be restored from the leader. The leader in turn was backed up at a secondary onshore site as part of the disaster recovery plan.
Consideration was also given to the fact that Asset Guardian regularly reviewed IEC 62443 and other relevant industry standards and that the Asset Guardian software was updated to meet these standards when required.
The IEC 62443 standard is wide ranging, covering all aspects of cyber security in the controls and automation industry. The use of Asset Guardian as a CSMS as part of the overall cyber security strategy ensured that the operator was adhering to this standard.